Mustansir G.
Cybersecurity Expert & Fullstack Engineer
CyferWall Director • Security-focused Fullstack Engineer for Early-Stage Companies
ABOUT
As a Cybersecurity Expert and Startup Fullstack Engineer, I specialize in building secure, scalable applications while ensuring robust cybersecurity practices. Currently serving as Director at CyferWall, I facilitate seamless collaboration between security teams and development teams to ensure both product security and business growth.
Leveraging my extensive experience in penetration testing, deepfake detection, and enterprise security, I make calculated decisions concerning security architecture and core technical components. My background includes leading Government of India funded research worth ₹15 lakhs, resulting in 9 SCOPUS-indexed papers and 1 granted patent for TrustTrace, our deepfake detection solution.
My unique combination of cybersecurity expertise and fullstack development enables me to strategically identify and implement security-first features that empower startups to evolve from initial prototypes (0.0.1) to production-ready, secure products (1.0.0) that can withstand modern cyber threats.
Specializations: Enterprise Cybersecurity, Penetration Testing, Deepfake Detection, Secure Application Development, CTF Design, Linux Security, Mobile Security, and Security Architecture for companies like BoultAudio, BeTimeFul, Engaze, and LinuxAdmin.
EXPERIENCE
Oct 2024 - June 2025 As the Tech Lead at Engaze, a Mumbai-based technology startup, I played a key role in product ideation and full-stack development. Led cross-functional teams in building scalable web applications while ensuring security best practices. Responsible for technical documentation, feature planning, user experience optimization, and security implementation across all development phases.
- Full-Stack Development
- Software Architecture
- Team Leadership
- Security Implementation
- Technical Documentation
Apr 2024 - Present At CyferWall, I'm innovating and building next-generation cybersecurity products through our SAAS platform. Leading product development for enterprise security solutions that help companies scale their cybersecurity infrastructure. CyferWall specializes in automated security monitoring, threat detection, and compliance management for growing businesses.
- Cybersecurity SAAS
- Product Strategy
- Security Architecture
- Threat Detection
- Market Research
- Enterprise Security
Oct 2023 - Mar 2024 Mentored a Government of India (GoI) funded research project worth ₹15 lakhs focused on protecting against deepfake attacks and AI-generated content threats. Led a team of 4 junior research fellows in developing innovative deepfake detection algorithms, resulting in 9 SCOPUS-indexed research papers and 1 granted patent. Successfully launched TrustTrace, a multi-modal deepfake prevention solution that detects manipulated video, audio, and image content.
- Deepfake Detection
- AI/ML Research
- Computer Vision
- Research Management
- Patent Development
- TensorFlow/PyTorch
Jun 2023 - Nov 2024 Full Stack Engineer & Security Specialist - Dynavate TechnologiesAs a software development agency, Dynavate helped major brands like BoultAudio (India's leading wearables brand) achieve their vision of creating a comprehensive wearable android application. Developed a secure, scalable solution to compete with Chinese apps while ensuring superior data privacy. The app connects to multiple watch models across different chipsets and operating systems, creating a unified wearable ecosystem built to scale to 1,000,000+ users with enhanced security and user experience.
- Android Development
- Wearables Integration
- Scalable Architecture
- Data Privacy
- Security Implementation
- IoT Connectivity
Apr 2023 - Jun 2023 Launched BeTimeFul 3.0 comprehensive productivity suite within 3 weeks of joining. Led full-stack development of mobile applications (iOS and Android), Chrome extension, and MacOS desktop application. Implemented secure payment solutions and user retention strategies that significantly improved user acquisition metrics. BeTimeFul focuses on digital wellness and productivity optimization.
- Mobile App Development
- Chrome Extension
- MacOS Development
- Payment Integration
- User Analytics
- Product Strategy
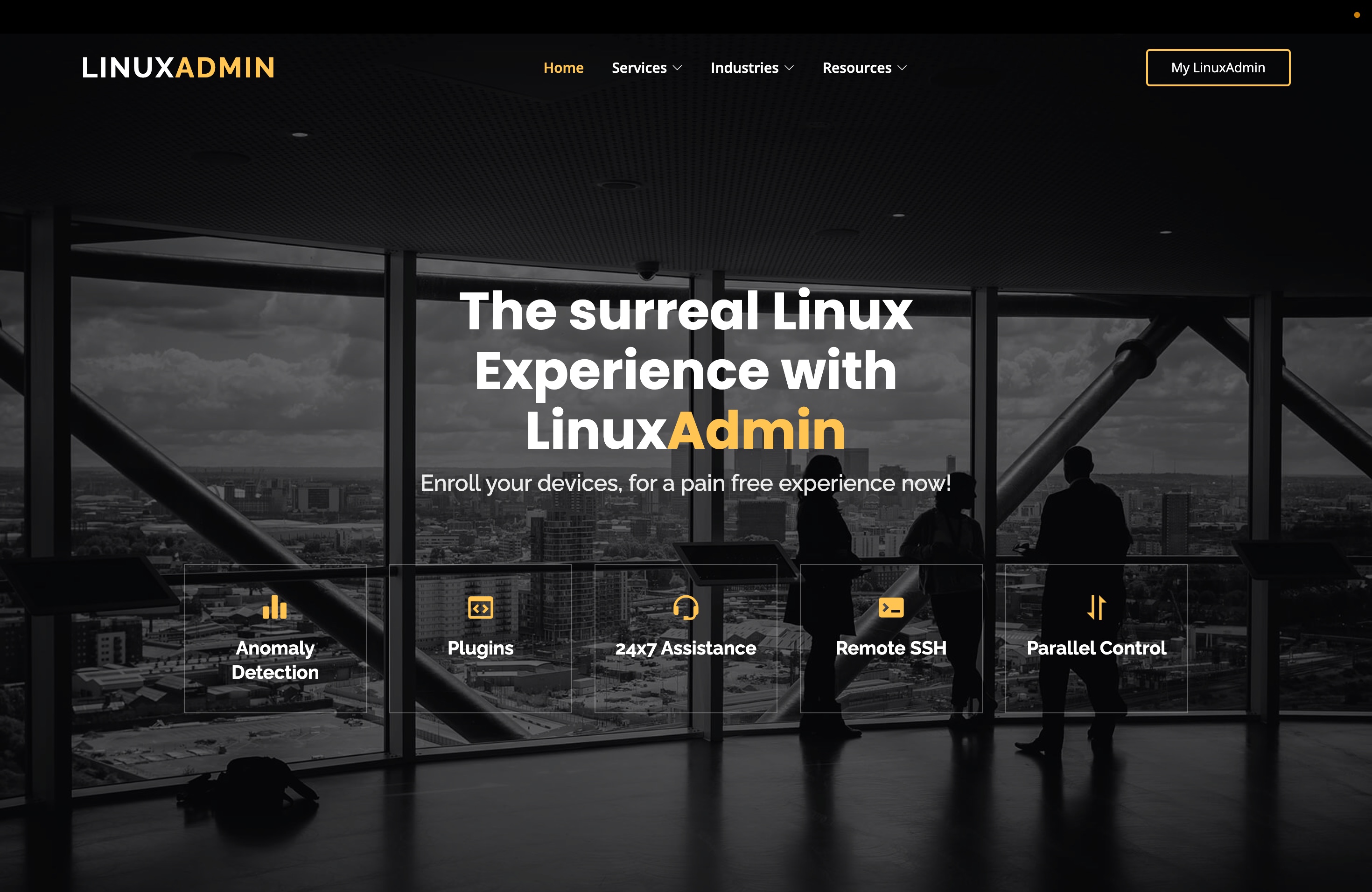
Aug 2022 - Aug 2023 Engineered LinuxAdmin, a comprehensive remote monitoring and management solution for Linux servers and devices from the ground up. Built entirely on free and open-source software with integrated Wazuh SIEM for advanced security monitoring and threat detection. Features include secure remote SSH access, parallel device control, 24x7 monitoring, and real-time security alerts. This solution helps organizations maintain secure Linux infrastructure while reducing operational costs.
- Linux Security
- Remote Monitoring
- Wazuh SIEM
- Open Source Solutions
- SSH Security
- System Administration
Jan 2023 - Apr 2023 Designed and developed 10+ Capture The Flag (CTF) challenges for the Global CyberPeace Challenge, an international cybersecurity competition. Created complex security scenarios across multiple domains including web application security, malware analysis, cryptography, buffer overflow exploits, and digital forensics. These CTFs helped train and assess cybersecurity professionals worldwide.
- CTF Development
- Web Security
- Malware Analysis
- Cryptography
- Buffer Overflow
- Digital Forensics
Jul 2022 - Aug 2022 Worked as a backend development engineer focusing on distributed systems and task processing using Celery. Managed comprehensive deployment infrastructure with Docker containerization and orchestration. Built and enhanced secure authentication platforms with multi-factor authentication and session management for enterprise clients.
- Backend Architecture
- Celery Task Processing
- Docker Deployment
- Authentication Systems
- DevOps
- API Security
Jan 2022 - Feb 2022 Created comprehensive internal training documentation and security assessment reports used to educate cybersecurity analysts on emerging vulnerabilities and threat landscapes. Authored technical content covering various cybersecurity domains including network security, application security, and incident response procedures.
- Security Documentation
- Vulnerability Assessment
- Technical Writing
- Security Training
- Threat Analysis
Sep 2021 - Mar 2022 Completed comprehensive cybersecurity training program focusing on ethical hacking and penetration testing methodologies. Gained hands-on experience with security assessment tools, vulnerability scanning, network security testing, and security incident response. This foundational training established my expertise in cybersecurity principles and practices.
- Penetration Testing
- Ethical Hacking
- Vulnerability Assessment
- Network Security
- Security Tools
- Incident Response
EDUCATION

Bachelor of Engineering in Cyber Security –Mumbai University ( Shah and Anchor Kutchhi Engineering College )
Focused on software engineering, algorithms, and web development. Participated in hackathons and student tech organizations.
Projects
LinuxAdmin
Remote monitoring and management platform for Linux devices.
- React
- Node.js
- Electron
- Linux
- WebSockets
- Tailwind
RSH
Quick solution for starting reverse shell listeners using multiple tools like nc, sc, etc.
- Python
- Shell
- Open Source
- CLI

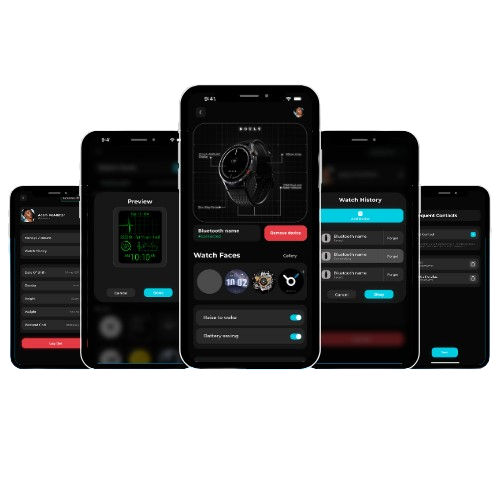
Boult One
Cross-platform mobile application to connect with moyoung and coding sdk based wearable devices.
- Flutter
- Dart
- Bluetooth
- Wearables
- Android
- iOS
Netaji
A poster making application built using a cross-platform language.
- Flutter
- Dart
- Canvas
- Cross-Platform
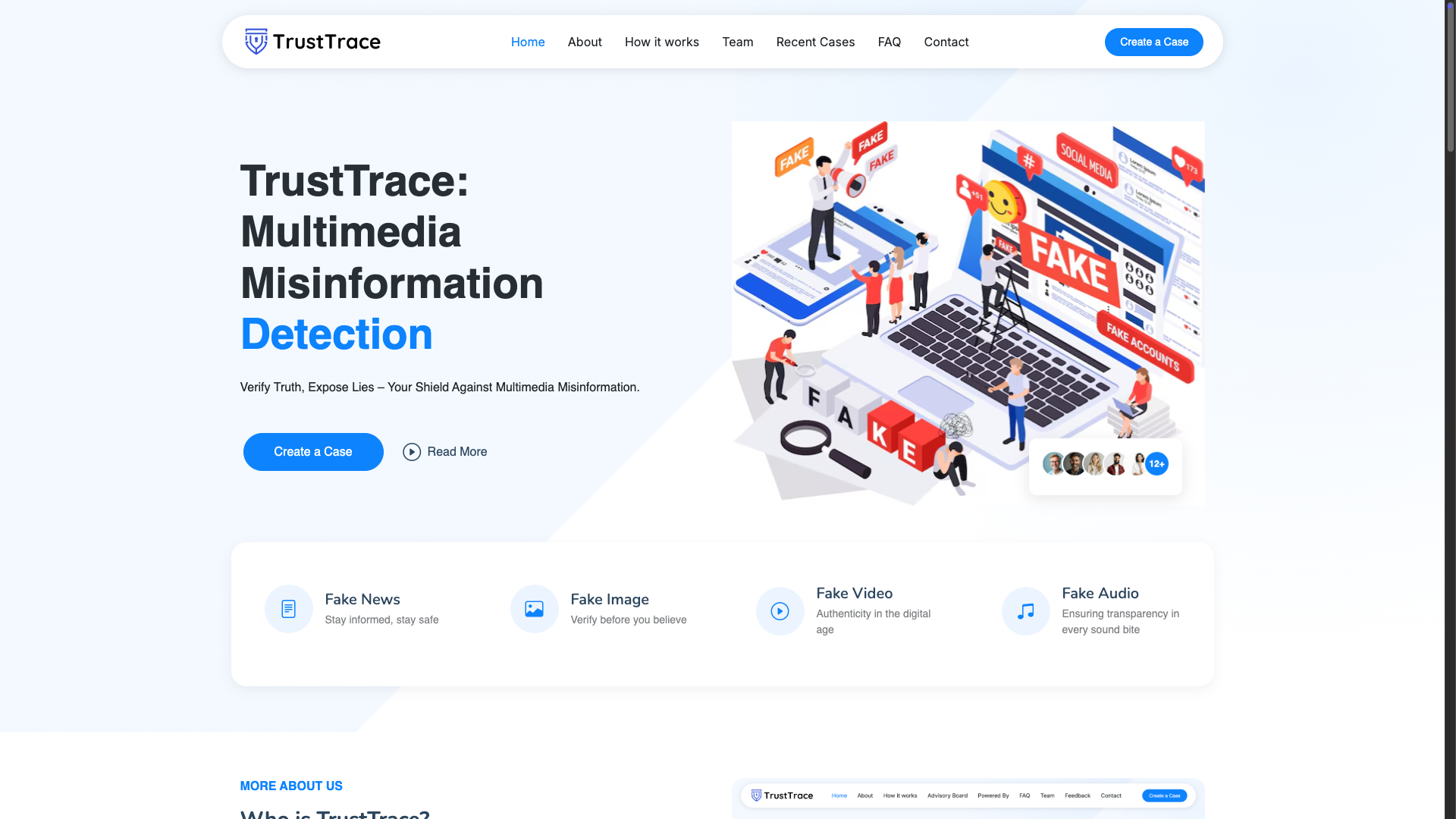
TrustTrace
Advanced deepfake detection solution for video, audio and images. 10+ SCOPUS indexed papers published, 1 patent published.
- Python
- Deep Learning
- TensorFlow
- OpenCV
- Research
BoultAudio Shopify
Shopify store for BoultAudio, one of India's fastest growing wearables brand.
- Shopify
- Liquid
- JavaScript
- E-commerce
BeTimeFul Mobile
An application meant to improve productivity by automatic blocking of applications.
- Flutter
- Dart
- Android
- iOS
- Productivity
BeTimeFul Web
A Chrome extension meant to improve productivity by restricting access to sites like Instagram, YouTube and more.
- JavaScript
- Chrome Extension
- Web
- Productivity
WORKS
- Patent
A deep-fake detection system and method for detecting potential misinformation spread through manipulated content
Dr. Nilakshi Jain, Maj. Vineet Kumar, Dr. Bhavesh Patel, Dr. Shwetambari Borade, Mr. Mustansir Godhrawala, Mr. Shubham Kolaskar, Mr. Yash Nagare, Mr. Pratham Shah, Mr. Jayan Shah — Patent No. 18/2024, 2024
Filed: Apr 10, 2024
A comprehensive system for detecting potential misinformation spread through manipulated multimedia content (video, audio, image). The system integrates advanced machine learning models for deepfake detection, assigns unique case IDs, provides secure…
- Deepfake Detection
- Multimedia Forensics
- Machine Learning
- Audio Analysis
- Video Analysis
- Image Analysis
- Cybersecurity
- EfficientNet
- ResNext50
- MFCC
- SVM
- Case Management
- Research Paper
ResNet50 DeepFake Detector: Unmasking Reality
Shwetambari Borade, Nilakshi Jain, Bhavesh Patel, Vineet Kumar, Mustansir Godhrawala, Shubham Kolaskar, Yash Nagare, Pratham Shah, Jayan Shah — Indian Journal of Science and Technology, 2024
This research presents a robust approach for detecting video deepfakes using ResNet50, enhanced with novel image scraping techniques to minimize errors and improve prediction accuracy. The model, trained on CelebDF and FaceForensics++ datasets, achie…
- Deepfakes
- Deep Learning
- GAN
- ResNet50
- FaceForensics++
- CelebDF
- Research Paper
Enhancing Audio Deepfake Detection using Support Vector Machines and Mel-Frequency Cepstral Coefficients
Nilakshi Jain, Shwetambari Borade, Bhavesh Patel, Vineet Kumar, Mustansir Godhrawala, Shubham Kolaskar, Yash Nagare, Pratham Shah, Jayan Shah — Journal of Harbin Engineering University, 2024
This paper presents a machine learning system designed to differentiate real from synthetic speech using a Support Vector Machine (SVM) classifier. Trained on the 'for-original' Fake-or-Real (FoR) dataset, which consists of over 195,000 genuine and c…
- Deepfake Detection
- Mel-Frequency Cepstral Coefficients (MFCCs)
- Support Vector Machine (SVM)
- Audio Analysis
- Feature Extraction
- Media Manipulation
- Scalability Challenges
- Responsible Technology Deployment
- Ethical Considerations
- Real-world Applicability
- Research Paper
Harmonizing Algorithms: An Approach to Enhancing Audio Deepfake Detection
Shwetambari Borade, Nilakshi Jain, Bhavesh Patel, Vineet Kumar, Yash Nagare, Shubham Kolaskar, Jayan Shah, Pratham Shah, Mustansir Godhrawala — International Journal of Intelligent Systems and Applications in Engineering (IJISAE), 2024
This research enhances audio deepfake detection by developing a real-time, highly accurate methodology that addresses technological and ethical gaps. The study integrates an MFCC-based SVM classifier (97.28% accuracy) and a Neural Network with attent…
- Audio Deepfake Detection
- Comparative Model Verification
- Ethical Audio Forensics
- Real-time Speech Authenticity
- SVM-Neural Network Fusion
- MFCC
- Attention Mechanisms
- Digital Media Integrity
- Research Paper
Advancements in Video Deepfake Detection: Integration of ResNet50, EfficientNetB7, and EfficientNetAutoAtt B4 Models
Shwetambari Borade, Nilakshi Jain, Bhavesh Patel, Vineet Kumar, Mustansir Godhrawala, Shubham Kolaskar, Yash Nagare, Pratham Shah, Jayan Shah — International Journal of Intelligent Systems and Applications in Engineering (IJISAE), 2024
This study presents a novel approach to deepfake video detection by integrating three state-of-the-art models: ResNet50, EfficientNetB7, and EfficientNetAutoAttB4. The ensemble model, trained on diverse datasets, demonstrates superior performance in…
- Convolutional Neural Networks
- Deepfakes
- Deep Learning
- EfficientNet
- GAN
- ResNet50
- Video Forensics
- Model Ensemble
- Knowledge Distillation
- Digital Media Integrity
- Research Paper
Improving Deepfake Audio Detection: A Support Vector Machine Approach with Mel-Frequency Cepstral Coefficients
Shwetambari Borade, Nilakshi Jain, Bhavesh Patel, Vineet Kumar, Mustansir Godhrawala, Shubham Kolaskar, Yash Nagare, Pratham Shah, Jayan Shah — International Journal of Intelligent Systems and Applications in Engineering (IJISAE), 2024
This paper presents a machine learning system designed to differentiate real from synthetic speech using a Support Vector Machine (SVM) classifier. Trained on the 'for-original' Fake-or-Real (FoR) dataset, which consists of over 195,000 genuine and c…
- Audio Analysis
- Deepfake Detection
- Feature Extraction
- Media Manipulation
- Mel-Frequency Cepstral Coefficients (MFCCs)
- Support Vector Machine (SVM)
- Research Paper
Deepfake Technology and Image Forensics: Advancements, Challenges, and Ethical Implications in Synthetic Media Detection
Nilakshi Jain, Shwetambari Borade, Bhavesh Patel, Vineet Kumar, Mustansir Godhrawala, Shubham Kolaskar, Yash Nagare, Pratham Shah, Jayan Shah — International Journal of Intelligent Systems and Applications in Engineering (IJISAE), 2024
This comparative analysis delves into the dynamic landscape of deepfake technology and its intricate relationship with image forensics. Focused on advanced machine learning methodologies such as autoencoders, GANs, and CNNs, the exploration reveals b…
- Deepfake Technology
- Detection Methods
- Ethical Concerns
- Image Forensics
- Machine Learning Methodologies
- Research Paper
Detecting Deepfakes: Exploring Machine Learning Models for Audio, Video, and Image Analysis
Nilakshi Jain, Shwetambari Borade, Bhavesh Patel, Vineet Kumar, Mustansir Godhrawala, Shubham Kolaskar, Yash Nagare, Pratham Shah, Jayan Shah — International Journal of Intelligent Systems and Applications in Engineering (IJISAE), 2024
This study investigates the field of deepfake detection with an emphasis on the use of machine learning techniques in image, video, and audio analysis. It compares the effectiveness of models such as Random Forests, Gradient Boosting Machines, Suppor…
- Deepfake Detection
- Machine Learning Techniques
- Audio Analysis
- Video Analysis
- Image Analysis
- Ensemble Learning
- Performance Analysis
- ResNet
- Random Forest
- SVM
- CNN
- Neural Networks
- Research Paper
Deepfake Detection Using EfficientNetB7: Efficacy, Efficiency, and Adaptability
Nilakshi Jain, Shwetambari Borade, Bhavesh Patel, Vineet Kumar, Mustansir Godhrawala, Shubham Kolaskar, Yash Nagare, Pratham Shah, Jayan Shah — International Journal of Intelligent Systems and Applications in Engineering (IJISAE), 2024
This research explores the efficacy of EfficientNetB7, a state-of-the-art Convolutional Neural Network (CNN) architecture, for detecting deepfake videos. The study investigates EfficientNetB7's ability to efficiently discern subtle visual cues indica…
- Deepfakes
- Convolutional Neural Networks
- EfficientNetB7
- Deepfake Datasets
- Machine Learning
- Video Analysis
- Compound Scaling
- Neural Architecture Search
- Research Paper
Securing Visual Integrity: An EfficientNetB4-Based Solution with Attention Layers and Siamese Training for Face Manipulation Detection in Videos
Nilakshi Jain, Shwetambari Borade, Bhavesh Patel, Vineet Kumar, Mustansir Godhrawala, Shubham Kolaskar, Yash Nagare, Pratham Shah, Jayan Shah — International Journal of Intelligent Systems and Applications in Engineering (IJISAE), 2024
This research addresses the challenge of detecting face manipulation in videos using an EfficientNetB4-based model enhanced with attention layers and Siamese training. The proposed approach leverages convolutional neural networks (CNNs) to identify s…
- Convolutional Neural Networks
- Deepfake
- Digital Media Forensics
- EfficientNetB4
- Face Manipulation Detection
- Attention Mechanisms
- Siamese Networks
- FaceForensics
- DFDC
- Video Analysis
MISCELLANEOUS
GDSC Volunteer
DevFest, MumbaiHacks, 2024
Volunteered as a mentor for the Google Developer Student Clubs (GDSC) at DevFest and MumbaiHacks.
Winner, 1st Place (₹30,000 prize)
KJSCE Hack 7.0, 2023
Built a social-media application for recruiters and IT professionals, and took home 1st place with a ₹30,000 award.
Technical Coordinator
CCTNS 2023 Delhi (National Crime Records Bureau), 2023
Served as Technical Coordinator for the Crime and Criminal Tracking Network and Systems (CCTNS) hackathon held at NCRB headquarters in Delhi.
Top 10 in 10+ Hackathons
CodeShastra, Lines of Code, SIH, etc., 2023
Placed in the top 10 across 10+ hackathons, including CodeShastra, Lines of Code, and the Smart India Hackathon.